WHAT DOES WIRELESS NETWORK SECURITY MEAN?
❏ Wireless network security is the process of designing, implementing and ensuring security on a wireless computer network.
❏ Wireless network security is also known as wireless security.
WIRELESS CONCEPTS
❏ Network technology is heading toward a new era of technological evolution through wireless technologies.
❏ Wireless networking is revolutionizing the way people work and play. By removing physical connections or cables, individuals can use networks in new ways to make data portable, mobile, and accessible.
❏ A wireless network is an unbounded data communication system that uses radio-frequency technology to communicate with devices and obtain data.
❏ This network frees the user from complicated and multiple wired connections using electromagnetic (EM) waves to interconnect two individual points without establishing any physical connection
SOME BASIC WIRELESS TERMINOLOGIES
❏ Global System for Mobile Communications (GSM): It is a universal system used for mobile data transmission in wireless networks worldwide.
❏ Bandwidth: It describes the amount of information that may be broadcast over a connection. Usually, bandwidth refers to the data transfer rate and is measured in bits (amount of data) per second (bps)
❏ Access point (AP): An AP is used to connect wireless devices to a wireless/wired network. It allows wireless communication devices to connect to a wireless network through wireless standards such as Bluetooth and Wi-Fi. It serves as a switch or hub between a wired LAN and wireless network.
❏ Basic service set identifier (BSSID): It is the media access control (MAC) address of an access point (AP) or base station that has set up a basic service set (BSS). Generally, users are unaware of the BSS to which they belong. When a user moves a device, the BSS used by the device could change because of a variation in the range covered by the AP, but this change may not affect the connectivity of the wireless device.
❏ Industrial, scientific, and medical (ISM) band: This band is a set of frequencies used by the international industrial, scientific, and medical communities.
❏ Hotspot: These are places where wireless networks are available for public use. Hotspots refer to areas with Wi-Fi availability, where users can enable Wi-Fi on their devices and connect to the Internet.
❏ Association: It refers to the process of connecting a wireless device to an AP.
❏ Service set identifier (SSID): An SSID is a 32-alphanumeric-character unique identifier given to a wireless local area network (WLAN) that acts as a wireless identifier of the network. The SSID permits connections to the desired network among available independent networks. Devices connecting to the same WLAN should use the same SSID to establish connections.
❏ Orthogonal frequency-division multiplexing (OFDM), Multiple input, multiple output-orthogonal frequency-division multiplexing (MIMOOFDM), Direct-sequence spread spectrum (DSS), Frequency-hopping spread spectrum (FHSS).
WHY ARE WIRELESS NETWORK USED ?
❏ Wireless networks use radio-wave transmission, which usually occurs at the physical layer of the network structure.
❏ With the global wireless communication revolution, data networking and telecommunication are fundamentally changing.
❏ Wi-Fi is a widely used technology in wireless communication across a radio channel.
❏ Devices such as personal computers, video game consoles, and smartphones use Wi-Fi to connect to a network resource such as the Internet via a wireless network AP.
ADVANTAGES OF WIRELESS NETWORK
❏ Installation is fast and easy without the need for wiring through walls and over the buildigs.
❏ Easily provides connectivity in areas where it is difficult to lay cables
❏ The network can be accessed from anywhere within the range of an AP.
❏ Public spaces such as airports, libraries, schools, and even coffee shops offer constant Internet connections through WLANS
DISADVANTAGES OF WIRELESS NETWORK
❏ Security may not meet expectations. (For eg : MITM attacks)
❏ The bandwidth suffers as the number of devices in the network increases
❏ Wi-Fi upgrades may require new wireless cards and/or APs.
❏ Some electronic equipment can interfere with Wi-Fi networks.
WIRELESS STANDARDS
Wireless standards are a set of services and protocols that dictate how your Wi-Fi network (and other data transmission networks) acts.
❏ 802.11: The 802.11 (Wi-Fi) standard applies to WLANs and uses FHSS or DSSS as the frequency-hopping spectrum. It allows an electronic device to establish a wireless connection in any network.
❏ 802.11a: It is the first amendment to the original 802.11 standard. The 802.11 standard operates in the 5 GHz frequency band and supports bandwidths up to 54 Mbps using orthogonal frequency-division multiplexing (OFDM), It has a high maximum speed but is relatively more sensitive to walls and other obstacles.
❏ 802.11b: IEEE extended the 802.11 standard by creating the 802.11b specifications in 1999. This standard operates in the 2.4 GHz ISM band and supports bandwidths up to 11 Mbps using direct-sequence spread spectrum (DSSS) modulation.
❏ 802.11d: The 802.11d standard is an enhanced version of 802.11a and 802.11b that supports regulatory domains. The specifications of this standard can be set in the media access control (MAC) layer.
❏ IEEE 802.11e: It is used for real-time applications such as voice, VoIP, and video To ensure that these time-sensitive applications have the network resources they need. 802.11e defines mechanisms to ensure quality of service (QoS) to Layer 2 of the reference model, which is the MAC layer.
❏ 802.11i: The IEEE 802.11i standard improves WLAN security by implementing new encryption protocols such as the Temporal Key Integrity Protocol (TKIP) and Advanced Encryption Standard (AES).
❏ 802.11n: The IEEE 802.11n is a revision that enhances the 802.11g standard with multiple-input multiple-output (MIMO) antennas. It works in both the 2.4 GHz and S GHz bands. Furthermore, it is an IEEE industry standard for Wi-Fi wireless local network transportation. Digital Audio Broadcasting (DAB) and WLAN use OFDM.
❏ 802.11ah: Also called Wi-Fi Halow, uses 900 MHz bands for extended-range Wi-Fi networks and supports Internet of Things (1oT) communication with higher data rates and wider coverage range than the previous standards.
❏ 802.11ac: It provides a high-throughput network at a frequency of 5 GHz. It is faster and more reliable than the 802.11n standard. Moreover, it involves Gigabit networking, which provides an instantaneous data-transfer experience.
❏ 802.11ad: The 802.11ad standard includes a new physical layer for 802.11 networks and works on the 60 GHz spectrum. The data propagation speed in this standard is much higher from those of standards operating on the 2.4 GHz and 5 GHz bands, such as 802.11n.
❏ 802.12: Media utilization is dominated by this standard because it works on the demand priority protocol. The Ethernet speed with this standard is 100 Mbps. Furthermore, it is compatible with the 802.3 and 802.5 standards. Users currently on those standards can directly upgrade to the 802.12 standard.
❏ 802.15: It defines the standards for a wireless personal area network (WPAN) and describes the specifications for wireless connectivity with fixed or portable devices.
❏ 802.15.1 (Bluetooth): Bluetooth is mainly used for exchanging data over short distances on fixed or mobile devices. This standard works on the 2.4 GHz band.
❏ 802.15.4 (ZigBee): The 802.15.4 standard has a low data rate and complexity. The specification used in this standard is ZigBee, transmits long- distance data through a mesh network. The specification handles applications with a low data rate of 250 Kbps, but its use increases battery life.
❏ 802.15.5: This standard deploys itself on a full-mesh or half-mesh topology. It includes network initialization, addressing, and unicasting.
❏ 802.16: The IEEE 802.16 standard is a wireless communications standard designed to provide multiple physical layer (PHY) and MAC options. It is also known as WiMax. This standard is a specification for fixed broadband wireless metropolitan access networks (MANS) that use a point-to-multipoint architecture.
Wi-Fi AUTHENTICATION MODES
There are many different methods you can use to authenticate wireless clients. Some of these methods are outdated and have security weaknesses. They have been replaced with newer, more secure authentication methods.
Open system authentication process:
Open authentication is one of the two authentication methods from the first 802.11 standard In this process, any wireless client that attempts to access a Wi-Fi network:-
1. Sends a request to the wireless AP for authentication.
2. The station sends an authentication management frame containing the identity of the sending station for authentication and connection with the other wireless station, which is the wireless AP.
3. The AP then returns an authentication frame to confirm access to the requested station,
4. Thereby completing the authentication process.


Shared key authentication process: In this process, each wireless station receives a shared secret key over a secure channel that is distinct from the 802.11 wireless network communication channels. The following steps illustrate the establishment of a connection in the shared key authentication process:
1. The station sends an authentication frame to the AP.
2. The AP sends a challenge text to the station.
3. The station encrypts the challenge text using its configured 64-bit or 128-bit key and sends the encrypted text to the AP.
4. The AP uses its configured Wired Equivalent Privacy (WEP) key to decrypt the encrypted text. The AP compares the decrypted text with the original challenge text. If they match, the AP authenticates the station.
5. The station connects to the network.
The AP can reject the station if the decrypted text does not match the original challenge text, then, the station will be unable to communicate with either the Ethernet network or the 802.11 networks.


Wi-Fi AUTHENTICATION MODES USING A CENTRALIZED AUTHENTICATION SERVER
The 802.1X standard provides centralized authentication. For 802.1X authentication to work in a wireless network,
1. The AP must be able to securely identify the traffic from a specific wireless client.
2. In this Wi-Fi authentication process, a centralized authentication server known as Remote Authentication Dial-in User Service (RADIUS) sends authentication keys to both the AP and the clients that attempt to authenticate with the AP.
3. This key enables the AP to identify a particular wireless clien


TYPES OF WIRELESS ANTENNAS
Antennas are an integral part of Wi-Fi networks. In addition to sending and receiving radio signals, they convert electrical impulses into radio signals and vice versa.
Unidirectional Antenna
A directional antenna can broadcast and receive radio waves from a single direction. In order to improve transmission and reception, the directional antenna’s design allows it to work effectively in only a few directions. This also helps in reducing interference.


Omnidirectional Antenna
Omnidirectional antennas radiate electromagnetic (EM) energy in all directions. It provides a 360° horizontal radiation pattern. They radiate strong waves uniformly in two dimensions, but the waves are usually not as strong in the third dimension. These antennas are efficient in areas where wireless stations use time-division multiple access technology. A good example for an omnidirectional antenna is the antenna used by radio stations. These antennas are effective for radio signal transmission because the receiver may not be stationary. Therefore, a radio can receive a signal regardless of its location.


Parabolic Grid Antenna
A parabolic grid antenna uses the same principle as a satellite dish, but it does not have a solid dish. It consists of a semi-dish in the form of a grid consisting of aluminum wires. Parabolic grid antennas can achieve very long-distance Wi-Fi transmissions through highly focused radio beams. This type of antenna is useful for transmitting weak radio signals over very long distances on the order of 10 miles. This enables attackers to obtain a better signal quality, resulting in more data to eavesdrop on, more bandwidth to abuse, and a higher power output, which is essential in Layer-1 denial-of-service (DoS) and man-in-the-middle (MITM) attacks. The design of this antenna saves weight and space, and it can receive Wi-Fi signals that are either horizontally or vertically polarized.


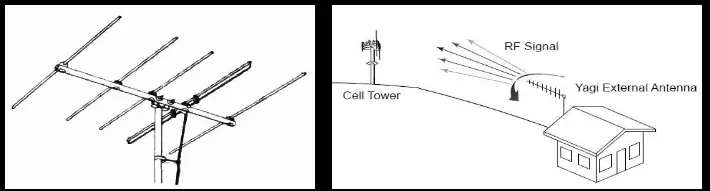
Yagi Antenna
A Yagi–Uda antenna or simply Yagi antenna, is a directional antenna consisting of two or more parallel resonant antenna elements in an end-fire array.
The Yagi antenna has gain allowing lower strength signals to be received. Furthermore, it not only has a unidirectional radiation and response pattern, but also concentrates the radiation and response. It consists of a reflector, dipole, and many directors. This antenna develops an and-fire radiation pattern

Reflector Antennas
Reflector antennas are used to concentrate EM energy that is radiated or received at a focal point. These reflectors are generally parabolic of the surface of the parabolic antenna is within a tolerance limit, it can be used as a primary mirror for all frequencies.
This can prevent interference while communicating with other satellites. A larger antenna reflector in terms of wavelength multiples results in a higher gain. Reflector antennas reflect radio signals and has a high manufacturing cost.


TYPES OF WIRELESS ENCRYPTION
Attacks on wireless networks are increasing daily with the increasing use of wireless networks.
The encryption of Information before it is transmitted on a wireless network is the most popular method of protecting wireless networks against attackers.
There are several types of wireless encryption algorithms that can secure a wireless network. Each wireless encryption algorithm has advantages and disadvantages.
❏ 802.111: It is an IEEE amendment that specifies security mechanisms for 802.11 wireless networks.
❏ WEP (Wired Equivalent Privacy): WEP is an encryption algorithm for IEEE 802.11 wireless networks. It is an old wireless security standard and can be cracked easily.
❏ EAP: The Extensible Authentication Protocol (EAP) supports multiple authentication methods, such as token cards, Kerberos, and certificates.
❏ LEAP: Lightweight EAP (LEAP) is a proprietary version of EAP developed by Cisco.
❏ WPA: It is an advanced wireless encryption protocol using TKIP and Message Integrity Check (MIC) to provide strong encryption and authentication. It uses a 48-bit initialization vector (V), 32-bit cyclic redundancy check (CRC), and TKIP encryption for wireless security.
❏ WPA2: It is an upgrade to WPA using AES and the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) for wireless data encryption.
❏ WPA3: It is a third-generation Wi-Fi security protocol that provides new features for personal and enterprise usage. It uses Galois/Counter Mode-256 (GCMP-256) for encryption and the 384-bit hash message authentication code with the Secure Hash Algorithm (HMAC-SHA-384) for authentication.
❏ TKIP: It is a security protocol used in WPA as a replacement for WEP.
❏ AESE: It is a symmetric-key encryption used in WPA2 as a replacement for TKIP.
❏ CCMP: It is an encryption protocol used in WPA2 for strong encryption and authentication.
❏ WPA2 Enterprise: It integrates EAP standards with WPA2 encryption.
❏ RADIUS: It is a centralized authentication and authorization management system.
❏ PEAP: It is a protocol that encapsulates the EAP within an encrypted and authenticated Transport Layer Security (TLS) tunnel


WIRELESS THREATS
ACCESS CONTROL ATTACKS
Access control attacks typically circumvent or bypass access control methods to steal data or user credentials. By collecting the latter, adversaries safely break access control by logging in as the authorized user and accessing his/her resources.
❏ WarDriving: In a wardriving attack, Attackers searching for wireless networks with vulnerabilities. An attacker who discovers a penetration point can launch further attacks on the LAN. Some of the tools that the attacker may use to perform wardriving attacks are KisMAC and NetStumbler.
❏ Rogue access points: In order to create a backdoor to a trusted network, an attacker may install an unsecured AP or fake AP inside a firewall. The attacker may also use software or hardware APs to perform this kind of attack. A wireless AP is termed a rogue access point when it is installed on a trusted network without authorization. An inside or outside attacker can install rogue APs on a trusted network with malicious intentions.
❏ AP misconfiguration (Human Error): If a user improperly configures any of the critical security settings at any of the APs, the entire network could be exposed to vulnerabilities and attacks. The AP cannot trigger alerts in most intrusion-detection systems, because these systems recognize them as a legitimate device.
❏ Ad hoc associations: An attacker may perform this kind of attack using any Universal Serial Bus (USB) adapter or wireless card. The attacker connects the host to an unsecured client to attack a specific client or to avoid AP security.
❏ Client mis-association: The client may intentionally or accidentally connect or associate with an AP outside the legitimate network because the WLAN signals travel through the air, walls, and other obstructions. This kind of client mis-association can lead to access control attacks.
❏ Promiscuous client: Using a promiscuous client, an attacker exploits the behavior of 802.11 wireless cards: they always attempt to find a stronger signal to connect. An attacker places an AP near the target Wi-Fi network and gives it a common SSID, offering an irresistibly stronger signal and higher speed than the target Wi-Fi network. The intent is to lure the client to connect to the attacker’s AP, rather than a legitimate Wi-Fi network.
Promiscuous clients allow an attacker to transmit target network traffic through a fake AP. It is very similar to the evil-twin threat on wireless networks, in which an attacker launches an AP that poses as an authorized AP by beaconing the WLAN’s SSID.
❏ Unauthorized association: Unauthorized association is a major threat to wireless networks. The prevention of this kind of attack depends on the method or technique that the attacker uses to get associated with a network.
INTEGRITY ATTACKS
An integrity attack involves changing or altering data during transmission.
In wireless integrity attacks, attackers send forged control, management, or data frames over a wireless network to misdirect wireless devices and perform another type of attack such as a DoS attack.
The below table summarizes different types of integrity attacks.


CONFIDENTIALITY ATTACKS
These attacks attempt to intercept confidential information sent over a wireless network, regardless of whether the system transmits data in cleartext or an encrypted format.
If the system transmits data in an encrypted format (such as WEP or WPA), an attacker may attempt to break the encryption. The below table summarizes different types of confidentiality attacks on wireless networks.


AUTHENTICATION ATTACKS
The objective of authentication attacks is to steal the identity of Wi Fi clients, their personal information, login credentials, etc. to gain unauthorized access to network resources. The below table summarizes different types of authentication attacks on wireless networks.


AVAILABILITY ATTACKS
Availability attacks aim at obstructing the delivery of wireless services to legitimate users, either by crippling WLAN resources or by denying them access to these resources.
This attack makes wireless network services unavailable to legitimate users. Attackers can perform availability attacks in various ways, obstructing the availability of wireless networks. The below table summarizes different types of availability attacks on wireless networks.